Unlock The Power Of Remote IoT: Connect, Control, And Secure Your Devices From Anywhere
In today's hyper-connected world, the Internet of Things (IoT) is transforming industries, homes, and even agriculture. From smart home devices that anticipate your needs to industrial sensors monitoring critical machinery, IoT devices are everywhere. But what happens when these devices are in remote locations, behind complex network configurations, or simply too numerous to manage individually? This is where the concept of "remote IoT" comes into play, offering a revolutionary way to connect, control, and secure your devices from literally anywhere on the planet. Imagine a world where you can monitor the performance of a solar panel array in a distant field, adjust the thermostat in your vacation home miles away, or troubleshoot an industrial robot without ever leaving your desk. This isn't science fiction; it's the reality that robust remote IoT solutions enable. 


What is Remote IoT and Why Does it Matter?
At its core, remote IoT empowers you to securely connect and manage machines and devices regardless of their physical location. The traditional challenges of remote access – dealing with complex port forwarding, dynamic IP addresses, and restrictive firewalls – are effectively eliminated. A well-implemented remote IoT solution acts as your secure gateway to your distributed network of devices. The significance of remote IoT cannot be overstated. In many scenarios, IoT devices operate independently in remote locations, far from a company's IT support team or your personal reach. This geographical dispersion, combined with the sheer volume of devices, makes traditional management methods impractical, if not impossible. Remote IoT provides the essential bridge, ensuring continuous oversight, efficient operation, and proactive problem-solving.The Pillars of Secure Remote IoT Connectivity
Security is paramount when dealing with remote devices, especially given the sensitive data they might handle or the critical infrastructure they might control. Remote IoT solutions prioritize security through several key mechanisms: * **Encrypted SSH Tunnels:** All network traffic between your management console and the remote device is encrypted via an SSH tunnel. This creates a secure, private conduit for data, ensuring that no one can read the information flowing through it – not even the remote IoT service provider itself. This level of encryption safeguards your data from potential eavesdropping and tampering. * **Firewall Traversal:** One of the biggest headaches in remote access is navigating firewalls. Remote IoT solutions are designed to connect to devices even when they are behind firewalls, bypassing the need for manual configuration or opening vulnerable ports. * **No Public IP Exposure:** Solutions like SocketXP are designed not to create any public IP addresses or ports as proxies. This significantly reduces the attack surface, as your devices are not directly exposed to the open internet, enhancing their security posture. * **P2P SSH for Enhanced Security:** For even greater security, connecting remote IoT devices to a central hub like a Raspberry Pi can be achieved using P2P (peer-to-peer) SSH software. This ensures data safety, privacy, and efficient management by establishing direct, encrypted connections without relying on intermediate public servers.Common Scenarios for IoT Remote SSH Connection
IoT remote SSH connections are versatile and find application across a wide range of industries and personal uses. Here are three common scenarios where this technology proves invaluable: 1. **Remote Monitoring and Management of Devices:** This is perhaps the most fundamental use case. Administrators can keep a constant eye on the performance, status, and health of devices, no matter where they are. This includes checking sensor readings, device uptime, resource utilization, and error logs. For instance, you could monitor the temperature and humidity in a remote agricultural greenhouse or check the operational status of smart city sensors. 2. **Remote Troubleshooting and Maintenance:** When a device malfunctions or requires an update, physical presence can be costly and time-consuming. Remote IoT allows engineers and technicians to securely access the device's command line (terminal access), control applications, and perform diagnostics remotely. This means they can restart services, push firmware updates, or even reconfigure settings without dispatching a team to the site, drastically reducing downtime and operational costs. 3. **Data Collection and Edge Management:** IoT devices generate vast amounts of data. Remote IoT facilitates the secure and efficient collection of this data from distributed devices. Furthermore, it enables "edge management," where certain processing or decision-making can occur directly on the device or a local gateway (like a Raspberry Pi) before data is sent to the cloud. This optimizes bandwidth usage and provides real-time insights closer to the source.Integrating Your Devices with Remote IoT Platforms
Getting started with remote IoT is often surprisingly straightforward, especially with popular platforms and devices.Raspberry Pi: Your Remote IoT Hub
The Raspberry Pi, with its versatility and low cost, is a popular choice for acting as a gateway or edge device in a remote IoT setup. After installing a remote IoT client, configuring your Raspberry Pi to work with the platform is typically a simple process. You might run a command to connect your device to your remote IoT account, enter your credentials, and once authenticated, your Raspberry Pi will appear in your remote IoT dashboard, ready for management. This makes it easy to securely connect remote IoT devices to your Raspberry Pi, ensuring data safety and privacy.Connecting to Devices Behind VPNs
In some enterprise setups, devices might be behind a VPN server. A remote IoT solution can still facilitate access. You connect to a VPN server, which acts as an intermediary between your management device and the IoT device’s network. The VPN server encrypts your internet traffic and assigns you a virtual IP address. Once connected to the VPN, you can access your IoT device using its local IP address, just as if you were physically connected to the same local network.Leveraging Cloud Platforms and Mobile Apps
The power of remote IoT extends to cloud integrations and mobile applications. For instance, if you're using an Arduino IoT setup, the Arduino IoT remote phone application lets you control and monitor all of your dashboards in the Arduino Cloud. With such apps, you can also access your phone's internal sensors like GPS data, light sensors, IMU, and more, depending on your phone's capabilities, adding another layer of data and control to your remote IoT ecosystem. For more complex deployments, especially in enterprise environments, securely connecting remote IoT devices within a VPC (Virtual Private Cloud) on platforms like AWS is crucial. Learning how to securely connect remote IoT VPC is not just a skill; it's a necessity to safeguard your entire network. A complete guide on setting up Ubuntu for IoT security or securely connecting remote IoT VPC with Raspberry Pi on AWS for free can provide invaluable insights into these advanced configurations.Beyond Basic Connectivity: Advanced Features
Modern remote IoT solutions offer features that go beyond traditional screen sharing or simple command-line access. These include: * **Terminal Access:** Direct command-line access to your remote devices for in-depth troubleshooting and configuration. * **App Control:** The ability to remotely launch, manage, and interact with applications running on your IoT devices. * **Edge Management:** Tools for managing software and processes directly on the edge devices, optimizing data flow and reducing latency. * **Remote Desktop Connection:** For devices with graphical interfaces, solutions like SocketXP IoT device remote access allow you to establish a remote desktop connection, enabling full visual control. You might simply enter `localhost` or `127.0.0.1` as the IP address and a specific port (e.g., 3000) on your RDC client to connect from an outside network over the internet.The Indispensable Need for Secure Remote IoT
While the benefits of remote IoT are clear, it's crucial to acknowledge the challenges. Continuous connection and data transmission can drain device batteries quickly, requiring frequent recharging or replacement. This highlights the importance of optimizing communication protocols and power management strategies. More importantly, securely connecting remote IoT devices is not just about protecting data; it's about safeguarding entire networks from potential breaches. Cyberattacks on IoT devices can lead to severe consequences, including data theft, financial loss, and even physical harm in critical infrastructure systems. Therefore, implementing robust security measures, understanding potential vulnerabilities, and staying updated on best practices for IoT security are absolutely vital.Conclusion
"Securely connect remote IoT" is more than just a catchy phrase; it's a powerful concept that is revolutionizing how we manage devices remotely. From controlling your smart home to monitoring industrial equipment or managing agricultural sensors from anywhere in the world, the possibilities are immense and often achievable without breaking the bank. By leveraging encrypted connections, bypassing network complexities, and integrating with versatile platforms like Raspberry Pi and cloud services, remote IoT empowers individuals and organizations to maintain control, ensure security, and unlock the full potential of their connected devices. It's about efficiency, security, and peace of mind in an increasingly connected world.Final Summary
This article explored the transformative power of remote IoT, emphasizing its ability to securely connect and manage devices from any location. We delved into the core functionalities, such as encrypted SSH tunnels and firewall traversal, which eliminate common connectivity hurdles like complex port forwarding. Key scenarios, including remote monitoring, troubleshooting, and data collection, were highlighted to showcase the practical applications. The article also covered how to integrate popular platforms like Raspberry Pi and leverage cloud services and mobile apps for enhanced control. Finally, it underscored the critical importance of robust security measures to protect against cyber threats and ensure the integrity of remote IoT networks.
Remote Connect IoT: Unlocking The Power
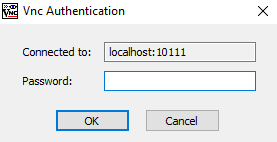
Remotely Connect to IoT via VNC : A Step-by-Step Guide
IoT Devices Remote Task Guide: Stay in Control Anywhere